
In a time when personal data is more valuable than ever, businesses cannot afford to lose customer trust over privacy concerns. However, trust isn’t just earned through excellent service – it’s built on the foundation of how businesses handle customer data, and digital trust is the new currency in customer relationships.
As customers grow more aware and protective of their personal information, companies must prioritize data privacy to meet social standards. In this landscape, trust becomes a key differentiator, where transparency, security, and ethical data use define whether a brand is viewed as reliable or risky, turning cautious customers into loyal ones.
The Intersection of Data Privacy and Customer Experience
At the crossroads of data privacy and customer experience lies a powerful truth: how a company handles personal information can make or break the customer’s journey.
Businesses regularly collect user data such as email addresses, biometrics, and credit card numbers. Supporting data privacy means obtaining user consent and protecting data from misuse. (IBM)
Consumers expect and demand transparency and control over their data. When privacy is prioritized, customers feel respected and secure, which in turn enhances their loyalty and satisfaction.
By providing transparency, data minimization, and user control, it can help ensure a positive experience for the customer.
Understanding Cybersecurity Risks in a Remote Work Environment
As remote work becomes the new normal, cybersecurity risks have surged, posing significant challenges for businesses and employees.
Remote customer service teams face unique cybersecurity challenges due to their direct interaction with sensitive customer data and the need to maintain secure communication channels.
Here are some of the most common cybersecurity risks associated with remote work according to TechTarget
- Challenges in complying with data regulations
- Increased susceptibility to phishing and other social engineering attacks
- Increased vulnerability to AI-driven attacks
- Unsecured and vulnerable hardware
- Unsecured and vulnerable networks
- Networks shared with other vulnerable devices
- Webcam hacking and zoom-bombing
The risk of insider threats also increases, as managing permissions can be complicated without strong monitoring systems. Without the protection of on-site security protocols, companies must implement strict cybersecurity measures, including VPNs, multi-factor authentication, and continuous employee training to protect the company and customer data. The remote work era demands vigilance and proactive strategies to lessen these evolving risks.
Trust and Distrust: Navigating the Digital Landscape
Navigating trust in the digital world is like online dating: everything looks promising until you take the plunge, and suddenly, you’re wondering if you just shared your secrets with a price – or a catfishing scam artist!
Trust and distrust coexist in a delicate balance. While technology connects us more than ever, it also exposes us to privacy risks and security threats, leaving customers wary of sharing their personal information.
Companies must navigate this landscape carefully, as one misstep in data handling can shatter hard-earned trust. When personal information is compromised, customers may feel betrayed and wary of the company’s ability to protect them. This loss of trust can lead to negative publicity, lasting damage to a brand’s reputation, and significant customer turnover, pushing them to competitors they perceive as more secure.
The best way to rebuild trust is to respond quickly and transparently. This includes promptly notifying affected customers, offering clear explanations of the incident, and detailing the steps taken to lessen the impact. Consistent efforts and genuine accountability can rebuild trust even after a breach.
Embrace a Culture of Healthy Skepticism
As an employee, you must approach all incoming information with a healthy level of skepticism. Cyber attackers often use social engineering and misinformation tactics to breach organizational defenses.
“Your employees are your first line of defense. If they don’t know how to respond in a cybersecurity-conscious manner, your company is at risk.” – Hamed Saeed (CEO of Pango Group)
By learning not to take information at face value but instead to verify its authenticity, organizations can drastically reduce the risk of falling victim to phishing, impersonation, and other cyber threats.
Rely on verification methods like checking email addresses, using known communication channels, and consulting team members; question unexpected emails, urgent requests, and unfamiliar links.
This culture of distrust toward unverified information can be one of the strongest defenses against cyber-attacks.
Below are critical steps to verifying information and maintaining cybersecurity.
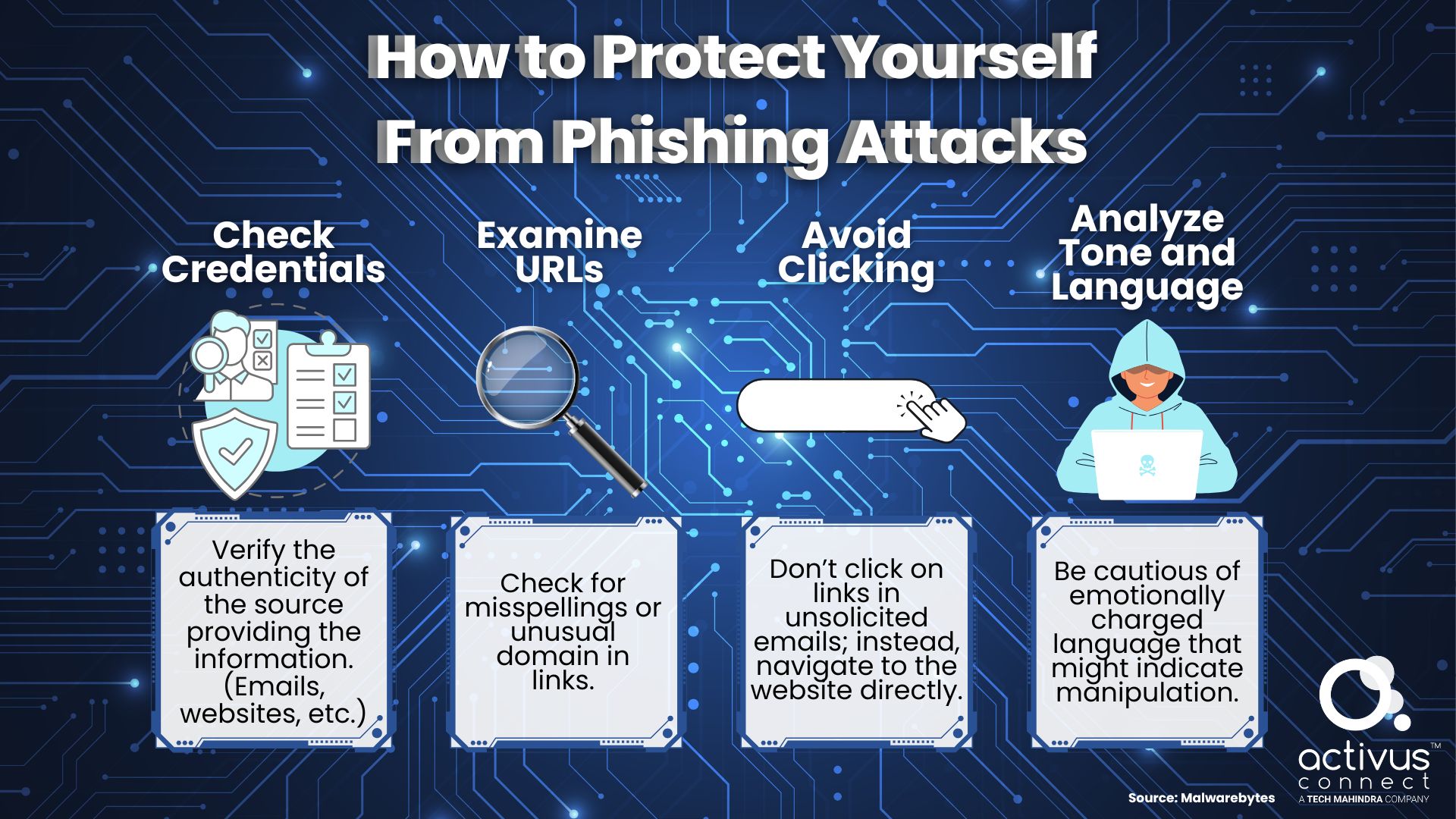
Implementing Vigilant Data Privacy Practices
Every layer of protection counts for keeping intruders at bay and building customer trust. In a world where data breaches hit the headlines daily, customers must feel their information is safe behind your walls.
Remote companies can take several proactive steps to strengthen data privacy, ensuring customer and company data remains secure. For starters, make sure a strong security policy is in place for the entire workforce.
Other strategies include investing in regular cybersecurity training, having encrypted workspaces, requiring multi-factor authentication, sending email traffic through cloud security, and utilizing a zero-trust model with strict authentication at each access point. (Forbes)
Continuous employee training and robust data encryption are essential pillars of data privacy. Employees are often the first line of defense against cyber threats. Regular training equips team members with up-to-date knowledge on identifying phishing attacks, managing passwords, and adhering to security protocols.
This vigilance reduces the risk of accidental data breaches and creates a dynamic defense against cyber threats, reinforcing trust and ensuring data privacy.
Conclusion: The Path Forward for Remote Customers Experience Companies
Data privacy has evolved beyond a legal checkbox – it’s now a strategic advantage that sets brands apart because, nowadays, data privacy defines trust.
When embedding data privacy into your customer experience strategy, you’re meeting regulatory demands and showing customers you genuinely value their security and peace of mind.
By prioritizing robust encryption, continuous employee training, and a culture of transparency, businesses can turn data security into a powerful foundation for long-lasting customer loyalty.
Embrace data privacy as a core component of your strategy and see it elevate your brand from merely compliant to genuinely customer-focused.
Are you ready to make data privacy a core part of your customer experience approach?