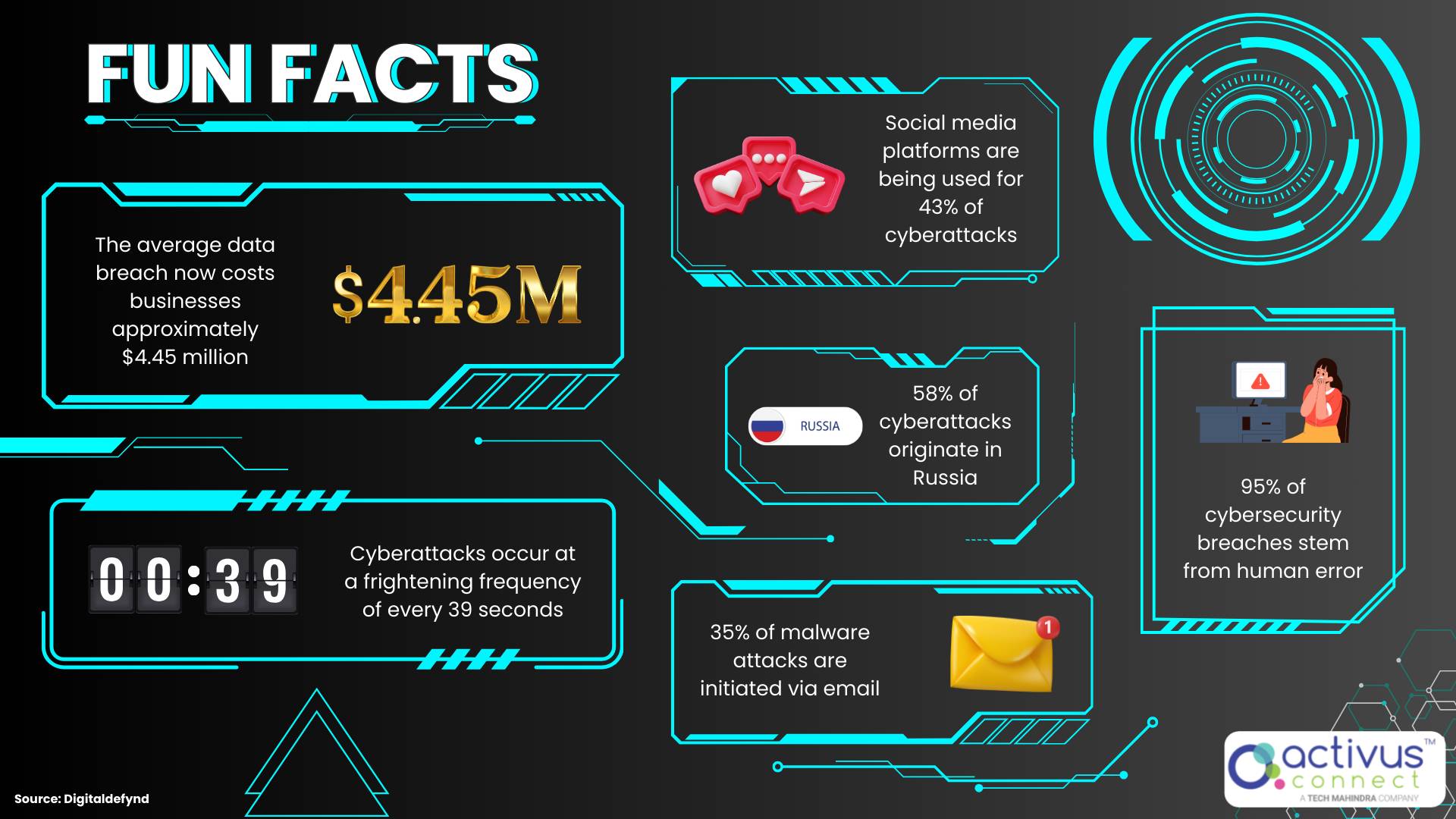
Did you know:
- In 2023, cyberattacks cost businesses over $8 trillion globally.
- Experts predict that by 2025, cybercrime could cause global damage exceeding $10.5 trillion annually. (Digitaldefynd)
These staggering numbers highlight a critical point: cybersecurity is no longer optional. Phishing, ransomware, and data breaches are becoming more frequent; no one is immune to the risk. Below is a helpful guide to walk you through the most common threats and how you can protect yourself in a digital world.
Technology’s Role in Cybersecurity
Technology plays a crucial role in cybersecurity, often acting like a superhero in a digital world filled with villains and supervillains.
Imagine technology as a highly trained, cyber-savvy bouncer at an exclusive club, armed with state-of-the-art gadgets and an eagle eye for suspicious characters.
While hackers try to pull off their latest heist, technology swoops in with its trusty antivirus software, firewalls, and encryption methods to save the day.
It’s like having a digital Swiss army knife ready to cut through malware and phishing attempts while reminding you to update your passwords more often than you change your socks.
In a world where cybercriminals are constantly trying to outsmart us, it’s comforting to know that technology is always on guard, even if it does tend to remind us to restart our computers at the most inconvenient times. But do you know what the most important factor is, it’s YOU! It is your Actions, it is your Behavior, it is your Partnership that allows the technology to function accordingly. Simply, YOU are critical to the success of fighting the villains.
Common Cybersecurity Threats
From online banking to social media, we constantly share sensitive information across multiple platforms. While this makes life more convenient, it also creates more opportunities for cybercriminals to exploit vulnerabilities in our deeply intertwined and hyper-connected world.
What you should look out for:
- Phishing – A type of cyberattack where attackers attempt to trick individuals into revealing sensitive information such as passwords, credit card numbers, or personal identification.
- Malware- (short for “malicious software”) refers to any software designed to disrupt, damage, or gain unauthorized access to a computer system. It comes in many forms, including viruses, ransomware, spyware, and worms, all of which can severely compromise devices and data.
- Social Engineering- Manipulation of individuals into divulging confidential information or performing actions that compromise security.
- Data Breaches- Occur when sensitive, protected, or confidential information is accessed or disclosed without authorization.
Importance of Personal Cyber Security
As we increasingly rely on online platforms in our daily lives, maintaining strong cyber security is crucial to protecting personal information and privacy. Cybercriminals often exploit weak security habits to steal sensitive information, commit identity theft, or install malicious software.
By incorporating simple yet effective security measures, individuals can safeguard their devices, data, and online identities from potential threats, ensuring their digital lives remain secure and private.

Cybersecurity Best Practices
Below are some helpful tips on how to help reduce your risk of falling victim to cyberattacks:
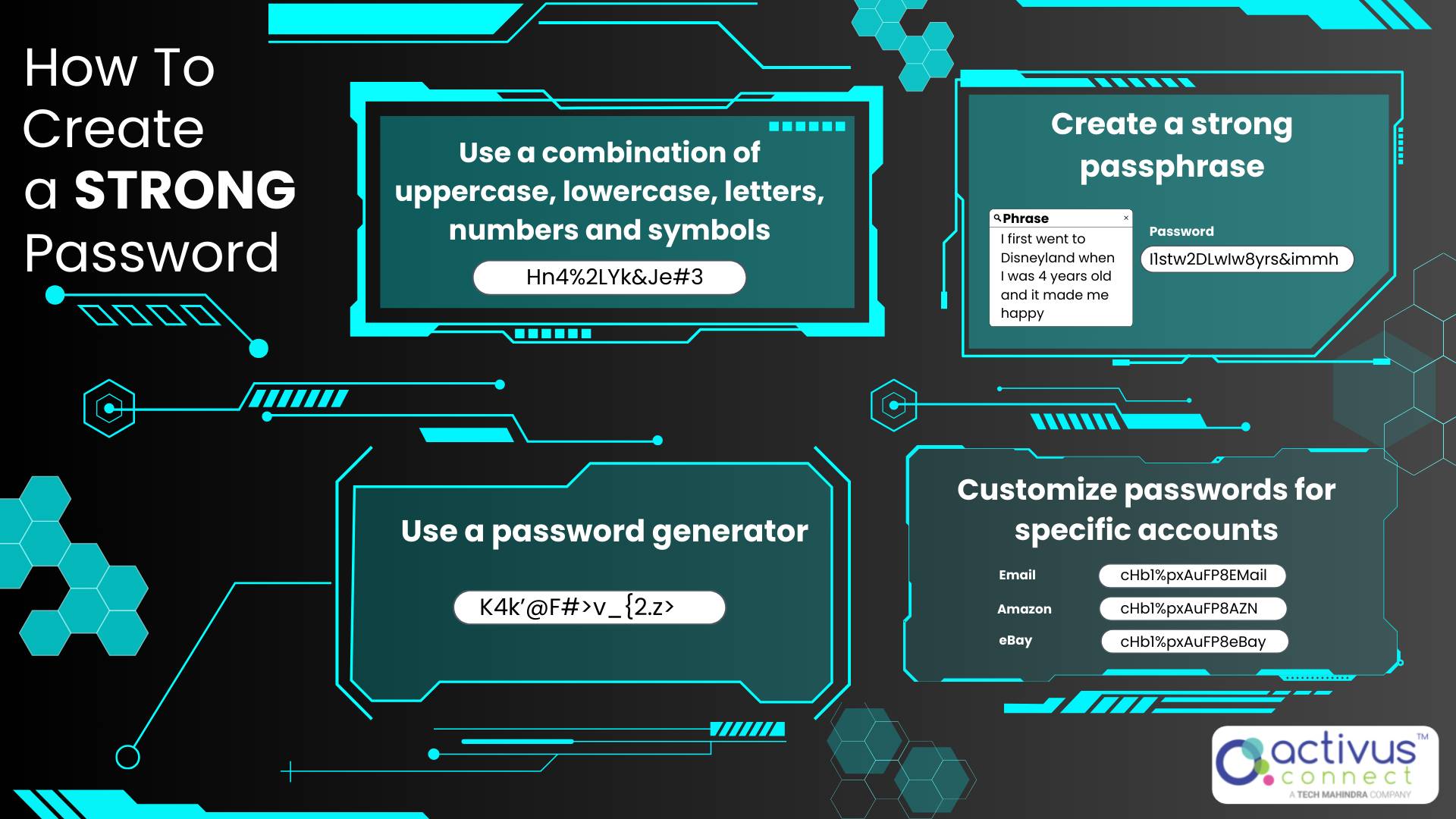
- Use strong and unique passwords
- Use upper and lower-case letters, numbers, and a symbol.
- Make passwords long and complex.
- Never reuse passwords.
- Have a minimum of 9 characters for your password.
- Enable multi-factor authentication
- Regularly update your software and operating system
- Learn to look both ways before crossing the street –in this case, it’s a digital highway filled with potential hackers creating potholes and faulty traffic signals to wreak havoc.
- Companies should continuously train their employees on what risks to look for.
Cyber awareness training is more than a “sit and listen” session; it’s more of a “let’s avoid a zombie apocalypse” seminar because nothing says “team bonding” like realizing you’re all one click away from a calamity of epic proportions (think “World War Z”).
Conclusion
In the grand scheme of things, in the wild world of the internet, staying safe is like keeping raccoons out of your trash – easy to forget until chaos hits!
But with a little effort (and maybe stronger digital locks), you can avoid the messy aftermath.
Remember, good cybersecurity habits aren’t just for tech wizards; they’re for anyone who doesn’t want their email hacked or their cat videos held for ransom.
So, be smart and take a moment out of your busy day, update your software, change that old password, and keep those cyber criminals out of our digital garbage!